Cybersecurity
Cybersecurity is the practice of protecting computer systems, networks, and data from a wide range of threats, including unauthorized access, data breaches, malware, viruses, and other cyberattacks. It encompasses a broad set of technologies, processes, and practices designed to safeguard information technology resources and ensure the confidentiality, integrity, and availability of data.
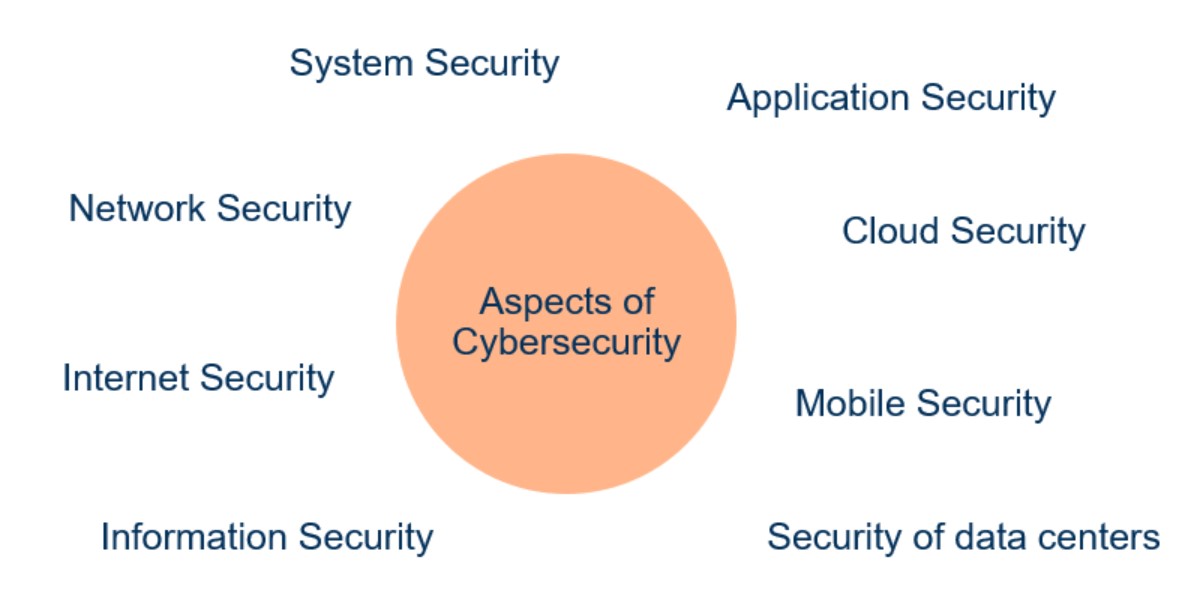
Key aspects of cybersecurity:
-
Types of Cybersecurity Threats:
- Malware: This includes viruses, worms, Trojans, ransomware, and spyware that can infect and compromise systems.
- Phishing: Cybercriminals use deceptive emails or messages to trick users into revealing sensitive information.
- Denial of Service (DoS) and Distributed Denial of Service (DDoS) Attacks: These attacks overwhelm a system or network, making it unavailable to users.
- Data Breaches: Unauthorized access to sensitive data, often resulting in its theft or exposure.
- Insider Threats: Malicious actions or negligence by employees or other trusted individuals within an organization.
- Social Engineering: Manipulating people into revealing confidential information or performing actions that compromise security.
-
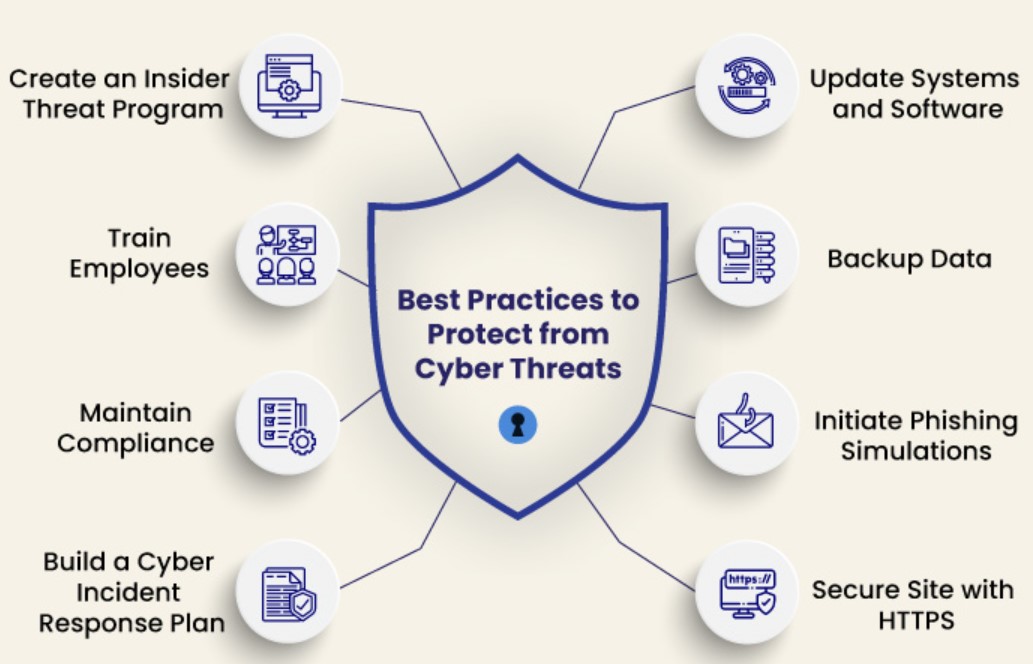
Cybersecurity Measures:
- Firewalls: Hardware or software-based systems that control incoming and outgoing network traffic to prevent unauthorized access.
- Antivirus Software: Detects and removes malware from systems.
- Encryption: Protects data by converting it into an unreadable format, which can only be decrypted with the correct key.
- Multi-factor Authentication (MFA): Requires users to provide multiple forms of identification to access a system or account.
- Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for suspicious activity and take actions to prevent intrusions.
- Patch Management: Regularly updating software and systems to address known vulnerabilities.
- Security Policies and Training: Establishing rules and educating users about cybersecurity best practices.
-
Security Layers:
- Network Security: Protects the network infrastructure from threats, such as firewalls, VPNs, and intrusion detection systems.
- Endpoint Security: Secures individual devices like computers, smartphones, and IoT devices.
- Application Security: Ensures that software and applications are developed and maintained with security in mind.
- Cloud Security: Protects data and resources stored in cloud services.
- Physical Security: Safeguards the physical access to data centers and critical infrastructure.
-
Compliance and Regulations:
- Many industries and regions have specific cybersecurity regulations and compliance standards that organizations must adhere to. Examples include GDPR in Europe, HIPAA in healthcare, and NIST in the United States.
-
Incident Response and Recovery:
- Developing plans and procedures to respond to cybersecurity incidents promptly and recover from them.
- This includes identifying the scope of the incident, mitigating damage, and restoring normal operations.
-
Cybersecurity Professionals:
- Experts in cybersecurity roles include security analysts, ethical hackers (penetration testers), security engineers, and Chief Information Security Officers (CISOs).
-
Emerging Trends:
- As technology evolves, so do cybersecurity threats. Some emerging trends include the rise of AI and machine learning in cybersecurity, increased focus on IoT security, and the expansion of remote work cybersecurity measures.
-
Challenges:
- The cybersecurity landscape is dynamic, and attackers are becoming more sophisticated. Organizations face challenges in keeping up with evolving threats, securing remote work environments, and managing the shortage of skilled cybersecurity professionals.
In summary, cybersecurity is a critical aspect of modern digital life, as it helps protect sensitive data, critical infrastructure, and privacy. Organizations and individuals must stay vigilant and continually adapt to new threats and technologies to maintain effective cybersecurity.
Implementing secure network designs
Implementing secure network designs is essential to protect an organization's sensitive data and ensure the confidentiality, integrity, and availability of network resources.
Here are steps and considerations for implementing secure network designs:
-
Define Security Requirements: Start by understanding your organization's security requirements and objectives. This includes identifying sensitive data, compliance regulations, and the specific threats you need to guard against.
-
Segmentation: Divide your network into segments or zones. Implement network segmentation to separate different types of traffic and user groups. This limits lateral movement for attackers if one segment is compromised.
-
Access Control: Enforce strict access controls. Implement role-based access control (RBAC), least privilege principles, and strong authentication mechanisms. Only authorized users should have access to specific resources.
-
Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS): Deploy firewalls to filter traffic at the network perimeter and between network segments. Use IDS/IPS to monitor and block suspicious or malicious network activities.
-
Virtual Private Networks (VPNs): Secure remote access and data transmission with VPNs. Ensure that data is encrypted during transit, and implement multi-factor authentication for VPN access.
-
Encryption: Use encryption protocols (e.g., SSL/TLS) to secure data in transit and encryption technologies to protect data at rest, such as on file servers and databases.
-
Monitoring and Logging: Implement robust network monitoring and logging. Continuously monitor network traffic, review logs, and set up alerting for suspicious activities. This helps detect and respond to security incidents.
-
Intrusion Detection and Response (IDR): Develop an incident detection and response plan. Have procedures in place to investigate and mitigate security incidents promptly.
-
Patch Management: Establish a patch management process to keep network devices, servers, and applications up to date with security patches. Vulnerabilities in outdated software can be exploited.
-
Network Security Policies: Define and enforce network security policies. These policies should specify acceptable use, password policies, data handling guidelines, and other security practices.
-
Redundancy and High Availability: Implement network redundancy and failover mechanisms to ensure that critical services are available even in the event of network failures or outages.
-
Security Awareness Training: Train employees and network administrators in security best practices. Security awareness is essential to prevent social engineering attacks and internal threats.
-
Third-Party Assessments: Regularly assess and audit your network security through third-party security assessments and penetration testing. These assessments can uncover vulnerabilities that might be missed internally.
-
Vendor Security: Assess the security of third-party vendors and service providers. Ensure that their products and services meet your security standards.
-
Network Documentation: Maintain up-to-date network documentation, including network diagrams, configurations, and inventory. This information is critical for troubleshooting and security audits.
-
Incident Response Plan: Develop a comprehensive incident response plan that outlines how to respond to security incidents, including data breaches and network compromises.
-
Regular Updates and Training: Security is an ongoing process. Stay informed about emerging threats and vulnerabilities, and update your network security measures and training accordingly.
Implementing secure network designs is an ongoing process that requires continuous monitoring, adaptation, and vigilance. Regular security assessments and testing can help ensure that your network remains resilient against evolving threats.
Implementing firewalls and proxy servers
Implementing firewalls and proxy servers is a fundamental part of network security to control and secure network traffic.
Here's a step-by-step guide on how to implement firewalls and proxy servers effectively:
1. Firewall Implementation:
Firewalls are designed to filter and control network traffic, protecting your network from unauthorized access and security threats.
a. Determine Firewall Type:
- Choose the type of firewall you need based on your specific requirements. Common types include packet-filtering firewalls, stateful firewalls, and next-generation firewalls (NGFW) with advanced features.
b. Define Security Policies:
- Develop a set of security policies and rules. Determine what traffic should be allowed and what should be blocked. Follow the principle of least privilege to minimize security risks.
c. Network Segmentation:
- Create distinct network zones, such as an internal network, DMZ (Demilitarized Zone), and external network. Configure firewall rules to control traffic between these zones.
d. Configure Logging and Monitoring:
- Enable logging and monitoring features on your firewall. Regularly review logs to identify and respond to security incidents and threats.
e. Update and Patch:
- Keep your firewall's firmware or software up to date with the latest security patches. This helps mitigate known vulnerabilities.
f. Conduct Regular Audits:
- Perform periodic security audits and penetration tests to ensure that your firewall rules and policies are effective in preventing unauthorized access.
2. Proxy Server Implementation:
Proxy servers act as intermediaries between client devices and the internet, providing control and security over internet access.
a. Choose Proxy Type:
- Decide whether you need a forward proxy (used by clients to access the internet) or a reverse proxy (used to protect web servers and applications).
b. Set Up Access Control:
- Define access control policies to determine which clients are allowed to use the proxy and what internet resources they can access. This can be accomplished through user authentication and authorization mechanisms.
c. Implement Content Filtering:
- Utilize content filtering to block or allow access to specific websites, web content, and applications based on categories or keywords, enforcing acceptable use policies.
d. SSL Inspection (if needed):
- Implement SSL inspection if necessary. This allows the proxy server to decrypt and inspect encrypted traffic for security threats and enforce security measures on encrypted content.
e. Caching:
- Enable caching to improve internet access speed by storing frequently accessed content locally. This reduces bandwidth usage and enhances user experience.
f. Logging and Monitoring:
- Configure logging and monitoring for proxy server activities. Analyze logs to detect suspicious activities and enforce security policies.
g. Load Balancing (for Reverse Proxies):
- If you are using a reverse proxy for web applications, consider implementing load balancing to distribute traffic across multiple servers for performance and redundancy.
h. Regular Updates and Patching:
- Keep the proxy server software up to date with the latest security patches and updates to protect against vulnerabilities.
i. Authentication and Single Sign-On (SSO):
- Implement user authentication and consider integrating the proxy server with single sign-on systems to streamline user access.
Both firewalls and proxy servers require careful design and maintenance to ensure that they effectively protect your network from threats. Regularly update and test these security measures to keep them robust against evolving threats.
Implementing secure application protocols
Implementing secure application protocols is crucial for ensuring the confidentiality, integrity, and authenticity of data exchanged between applications and services. Secure application protocols protect against various security threats, such as eavesdropping, data tampering, and man-in-the-middle attacks. Here are some steps to implement secure application protocols effectively:
-
Select Secure Protocols: Choose secure application-layer protocols that provide strong encryption and security features. Some common secure application protocols include HTTPS (for web applications), SSH (for secure shell access), and SFTP (for secure file transfer).
-
Use Strong Encryption: Implement strong encryption algorithms and ciphers to protect data in transit. For example, in HTTPS, use TLS (Transport Layer Security) with strong encryption algorithms like AES and RSA.
-
Implement Secure Authentication: Ensure that authentication mechanisms used in your application protocols are secure. Implement multi-factor authentication (MFA) where possible and avoid weak or deprecated authentication methods.
-
Certificate Management: If using SSL/TLS, manage digital certificates properly. Obtain certificates from trusted certificate authorities (CAs), keep them up to date, and monitor their expiration dates.
-
HSTS (HTTP Strict Transport Security): For web applications, enable HSTS to ensure that browsers communicate with your site over HTTPS only, preventing downgrade attacks.
-
OCSP Stapling: Implement OCSP stapling for SSL/TLS certificates to improve the verification process of certificate status, enhancing security and performance.
-
Content Security Policies (CSP): Use CSP headers in web applications to restrict content sources, reducing the risk of cross-site scripting (XSS) attacks.
-
Security Headers: Implement security headers, such as X-Content-Type-Options, X-Frame-Options, and X-XSS-Protection, to enhance the security of web applications.
-
Input Validation: Ensure that all data received from clients or external sources is validated and sanitized to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
-
Secure Session Management: Implement secure session management practices to protect user sessions. Use session tokens, ensure secure transmission, and enable secure session cookies.
-
API Security: When dealing with API endpoints, use secure authentication mechanisms, validate input, and implement authorization controls. Implement rate limiting and access controls to prevent abuse.
-
Secure File Transfers: If your application involves file transfers, use secure protocols like SFTP or SCP for data exchange, ensuring data is encrypted in transit.
-
Regular Security Audits and Testing: Conduct security audits, vulnerability assessments, and penetration testing to identify and address security weaknesses and vulnerabilities in your application protocols.
-
Security Documentation: Document security practices, configurations, and protocols. This documentation should serve as a reference for administrators and developers.
-
Security Training: Ensure that your development and operations teams receive security training and are aware of best practices for implementing secure application protocols.
-
Incident Response Plan: Develop an incident response plan to handle security incidents, breaches, or vulnerabilities related to application protocols effectively.
-
Regular Updates and Patching: Keep all components and libraries used in your application protocols up to date with the latest security patches to address known vulnerabilities.
Implementing secure application protocols is an ongoing process that requires vigilance and regular security assessments. By following best practices and staying informed about evolving threats, you can significantly enhance the security of your applications and services.
Here's a more detailed overview of each of these fundamental components within the context of cybersecurity:
-
Cryptography: Cryptography is a cornerstone of cybersecurity, providing the means to secure data and communications. In the context of cybersecurity, the fundamentals of cryptography include:
- Confidentiality: Cryptography ensures that data remains confidential by encrypting it, making it unreadable without the proper decryption key.
- Integrity: Cryptographic hash functions can verify data integrity by producing a unique hash value for a given dataset. Any changes to the data will result in a different hash value.
- Authentication: Cryptography helps establish the identity of parties involved in communication through mechanisms like digital signatures, where the sender's identity is verified.
- Non-repudiation: Digital signatures also provide non-repudiation, ensuring that the sender cannot deny sending a particular message or document.
- Key Management: Proper key management is essential to protect cryptographic systems. This includes key generation, distribution, storage, and rotation.
-
Cloud Security: Cloud security focuses on safeguarding data, applications, and infrastructure in cloud environments. Key cybersecurity aspects related to the cloud include:
- Data Encryption: Ensuring data is encrypted both in transit and at rest within the cloud environment.
- Identity and Access Management (IAM): Controlling access to cloud resources through robust authentication, authorization, and role-based access control.
- Compliance and Regulations: Meeting regulatory requirements and compliance standards specific to the industry in which the organization operates.
- Security Monitoring and Incident Response: Continuously monitoring cloud resources and having a plan in place to respond to security incidents.
- Configuration Management: Ensuring that cloud resources are configured securely to prevent vulnerabilities.
- Cloud Provider Security: Understanding the security features provided by cloud service providers (e.g., AWS, Azure, Google Cloud) and the shared responsibility model.
-
Network Security: Network security is a fundamental aspect of cybersecurity, as it protects the integrity, confidentiality, and availability of data transmitted over networks. Key network security considerations include:
- Firewalls: Using firewalls to filter and control incoming and outgoing network traffic, based on predefined security policies.
- Intrusion Detection and Prevention Systems (IDS/IPS): Monitoring network traffic for suspicious activities and taking actions to prevent or mitigate threats.
- Virtual Private Networks (VPNs): Creating secure, encrypted connections for remote access and ensuring the confidentiality of data transmitted over public networks.
- Access Control: Implementing access control measures to restrict unauthorized access to network resources through authentication, authorization, and network segmentation.
- Security Policies and Procedures: Developing and enforcing network security policies and procedures within an organization.
- Patch Management: Regularly updating and patching network devices and software to mitigate known vulnerabilities.
Understanding these fundamentals in the context of cybersecurity is essential for designing, implementing, and maintaining robust security measures that protect an organization's digital assets and maintain the confidentiality, integrity, and availability of data and systems. Cybersecurity professionals must continually adapt to evolving threats and technologies to ensure comprehensive protection.
Enroll Now
- Cybersecurity
- Penetration Testing