Penetration Testing Overview
Penetration testing, often referred to as pen testing, is a critical component of cybersecurity that involves simulating cyberattacks on a computer system, network, or application to identify vulnerabilities and weaknesses. The primary purpose of penetration testing is to assess the security posture of an organization and help it improve its defenses by identifying and addressing security issues before malicious hackers can exploit them.
Some key aspects of penetration testing in cybersecurity:
-
Types of Penetration Testing:
- Black Box Testing: Testers have no prior knowledge of the target system. This simulates a real-world scenario where an attacker has little to no information about the target.
- White Box Testing: Testers have complete knowledge of the target system, including architecture, source code, and internal details.
- Gray Box Testing: Testers have partial knowledge of the target system, simulating a scenario where an insider may have some knowledge of the system.
-
Stages of Penetration Testing:
- Reconnaissance: Gathering information about the target, such as IP addresses, domain names, and open ports.
- Scanning: Identifying open ports and services running on the target system.
- Enumeration: Gathering more detailed information about the services and users.
- Exploitation: Attempting to exploit vulnerabilities to gain unauthorized access.
- Post-Exploitation: Maintaining access, pivoting to other systems, and escalating privileges.
- Reporting: Documenting findings, vulnerabilities, and recommended mitigations.
-
Common Vulnerabilities Tested:
- Network vulnerabilities: Testers look for misconfigurations, open ports, unpatched systems, and weak authentication.
- Web application vulnerabilities: This includes testing for SQL injection, cross-site scripting (XSS), and other web-related security issues.
- Wireless network vulnerabilities: Assessing the security of wireless networks and access points.
- Social engineering: Testing human factors, such as the susceptibility of employees to phishing attacks.
-
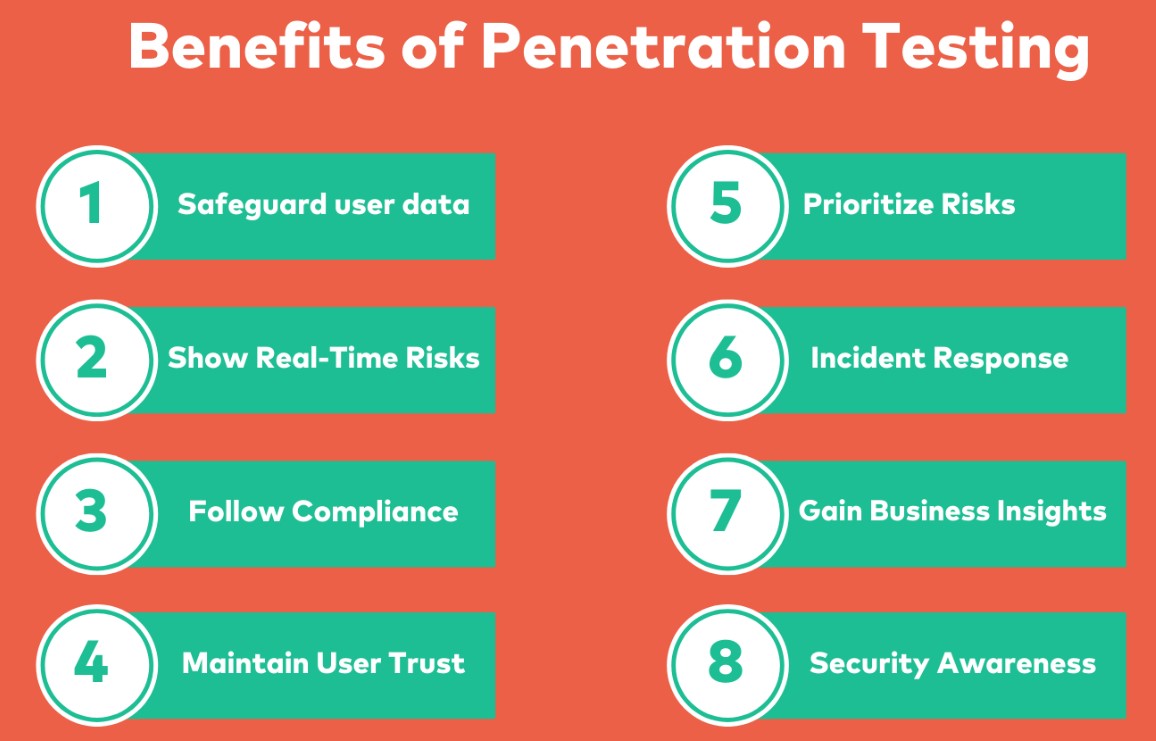
Benefits of Penetration Testing:
- Identifying vulnerabilities before attackers can exploit them.
- Providing a realistic assessment of an organization's security posture.
- Helping organizations prioritize and remediate security issues.
- Complying with regulatory requirements.
- Enhancing customer and stakeholder trust in an organization's security measures.
-
Penetration Testing Tools: There are various tools available for conducting penetration tests, including open-source and commercial tools like Metasploit, Nmap, Wireshark, Burp Suite, and many others.
-
Legal and Ethical Considerations: Penetration testing must be conducted within legal and ethical boundaries. Organizations should obtain proper authorization before conducting tests, and testers should follow a code of ethics.
-
Continuous Testing: Penetration testing should be an ongoing process, as new vulnerabilities can emerge as systems and technologies evolve. Regular testing helps ensure that an organization's security remains robust.
Penetration testing is a crucial element of a comprehensive cybersecurity strategy, providing organizations with insights into their security weaknesses and helping them take proactive measures to protect their digital assets from cyber threats.
Penetration testing, also known as pen testing or ethical hacking, is a simulated cyberattack that is carried out by a security professional to identify weaknesses in an organization's security posture. Pen testers use the same tools and techniques as malicious actors to gain unauthorized access to systems, networks, and applications.
The goal of a pen test is to find and exploit vulnerabilities before they can be used by attackers. Pen tests can be conducted on a variety of targets, including:
- Web applications
- Mobile applications
- Network infrastructure
- Databases
- Cloud environments
- Social engineering
Pen tests are typically conducted in a phased approach:
- Reconnaissance: The pen tester gathers information about the target system, such as its IP address, domain name, and operating system.
- Scanning: The pen tester uses automated tools to scan the target system for vulnerabilities.
- Gaining access: The pen tester attempts to exploit vulnerabilities in the target system to gain unauthorized access.
- Maintaining access: Once the pen tester has gained access to the target system, they attempt to maintain their access for as long as possible.
- Reporting: The pen tester documents their findings and provides recommendations for remediation.
Pen testing is a valuable tool for organizations that are serious about protecting their security. By identifying and remediating vulnerabilities before they can be exploited, organizations can reduce their risk of a data breach or other cyberattack.
Benefits of penetration testing
- Identifies security weaknesses before they can be exploited by attackers
- Provides a realistic assessment of an organization's security posture
- Helps organizations prioritize their security efforts
- Demonstrates to customers and stakeholders that an organization is committed to security
- Can be used to meet compliance requirements
Types of penetration testing
- Black box testing: The pen tester is not given any information about the target system.
- White box testing: The pen tester is given full access to the target system, including its source code.
- Gray box testing: The pen tester is given some information about the target system, but not full access.
Penetration testing methodologies
- Web application penetration testing: Tests for vulnerabilities in web applications.
- Mobile application penetration testing: Tests for vulnerabilities in mobile applications.
- Network penetration testing: Tests for vulnerabilities in network infrastructure.
- Database penetration testing: Tests for vulnerabilities in databases.
- Cloud penetration testing: Tests for vulnerabilities in cloud environments.
- Social engineering penetration testing: Tests for vulnerabilities in human behavior.
Penetration testing tools
- Nmap: A port scanner used to identify open ports on a target system.
- Nessus: A vulnerability scanner used to identify known vulnerabilities on a target system.
- Metasploit: A penetration testing framework that provides a wide range of exploit modules.
- Burp Suite: A web application security testing tool that provides a variety of features for testing web applications.
- Wireshark: A network protocol analyzer that can be used to capture and analyze network traffic.
Penetration testing certifications
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- Offensive Security Certified Professional (OSCP)
- Global Information Assurance Certification (GIAC) Penetration Tester (GPEN)
Penetration testing is a critical component of any comprehensive security program. By regularly conducting pen tests, organizations can identify and remediate vulnerabilities before they can be exploited by attackers.
Penetration testing, also known as pen testing, requires a variety of tools to identify and exploit vulnerabilities in a system, network, or application. These tools help cybersecurity professionals simulate attacks and assess the security of their environments.
Some commonly used penetration testing tools:
-
Metasploit: Metasploit is one of the most popular penetration testing frameworks. It offers a wide range of exploit modules, payloads, and auxiliary tools, making it an essential tool for penetration testers and security professionals.
-
Nmap (Network Mapper): Nmap is a powerful open-source network scanning tool that helps discover open ports, services, and hosts on a network. It can be used for both reconnaissance and vulnerability assessment.
-
Wireshark: Wireshark is a network protocol analyzer that allows you to capture and inspect network traffic. It's valuable for analyzing network communications and identifying security issues.
-
Burp Suite: Burp Suite is a web vulnerability scanner and proxy tool for testing web applications. It can help identify and exploit vulnerabilities like SQL injection, cross-site scripting (XSS), and more.
-
OWASP ZAP (Zed Attack Proxy): ZAP is another web application security testing tool that focuses on finding and fixing vulnerabilities in web applications. It's open source and maintained by the Open Web Application Security Project (OWASP).
-
Nessus: Nessus is a widely used vulnerability scanner that helps identify security issues in networks, systems, and applications. It offers a comprehensive database of known vulnerabilities.
-
Aircrack-ng: Aircrack-ng is a suite of tools for assessing the security of Wi-Fi networks. It can be used for network packet capturing, password cracking, and more.
-
John the Ripper: John the Ripper is a powerful password cracking tool that can be used to crack various password hashes using different attack methods.
-
Hydra: Hydra is a versatile password cracking tool that supports a wide range of network protocols and services, making it useful for testing weak credentials.
-
SQLMap: SQLMap is an open-source tool for detecting and exploiting SQL injection vulnerabilities in web applications and databases.
-
DirBuster: DirBuster is a directory and file brute-forcing tool used to discover hidden directories and files on web servers.
-
Gobuster: Gobuster is another directory and file brute-forcing tool designed to find hidden content on web servers and applications.
-
Snort: Snort is an open-source intrusion detection system (IDS) that can be used for monitoring and analyzing network traffic for signs of attacks and anomalies.
-
Netcat: Netcat, often referred to as the "Swiss Army knife" of networking, is a versatile networking utility for port scanning, banner grabbing, and creating reverse shells.
-
Aircrack-ng: Aircrack-ng is a collection of tools for auditing wireless networks. It can be used to capture packets, crack WEP and WPA/WPA2-PSK keys, and perform various wireless network-related tasks.
It's essential to note that the choice of penetration testing tools depends on the specific needs of the assessment and the environment being tested. Moreover, ethical and responsible use of these tools is paramount, and they should be employed only with proper authorization and adherence to relevant legal and ethical guidelines.

Enroll Now
- Cybersecurity
- Penetration Testing