Transport Layer Security (TLS) handshake
The Transport Layer Security (TLS) handshake is a critical component of the TLS protocol, which is designed to provide secure communication over a computer network.
The TLS handshake is responsible for establishing a secure connection between a client and a server. This secure connection is crucial for protecting the confidentiality and integrity of the data being exchanged.
Overview of the TLS handshake process:
-
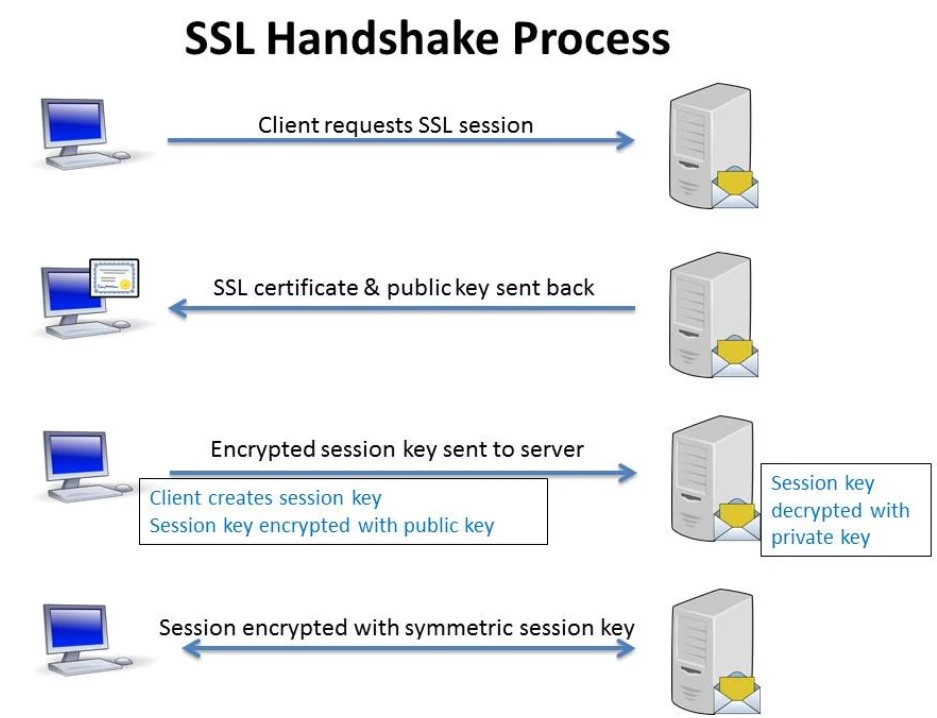
ClientHello:
- The TLS handshake begins with the client sending a "ClientHello" message to the server.
- This message includes information such as the TLS version supported by the client, a list of supported cryptographic algorithms (cipher suites), and other parameters.
-
ServerHello:
- Upon receiving the "ClientHello" message, the server responds with a "ServerHello" message.
- The server selects the highest TLS version that both the client and server support and chooses a cipher suite from the client's list of supported cipher suites.
- The "ServerHello" message also includes the server's digital certificate (if required) and other parameters.
-
Authentication and Key Exchange:
- If the server provides a digital certificate, the client verifies the certificate's authenticity using a process called certificate validation.
- The client may also send a "ClientKeyExchange" message, which contains information necessary for key exchange.
-
Key Derivation:
- Both the client and server use the exchanged information to derive pre-master secret.
- The pre-master secret is then used to generate the master secret.
-
Finished:
- Both the client and server send a "Finished" message to indicate that the handshake is complete.
- The "Finished" message is encrypted and authenticated using the newly established keys.
- Once both parties have exchanged "Finished" messages, the secure session is established, and they can begin to securely exchange data.
-
Secure Data Exchange:
- With the handshake complete, the client and server can now exchange data over a secure and encrypted connection using the established keys.
The TLS handshake ensures that the client and server can agree on a secure communication channel and exchange cryptographic parameters to establish keys for encrypting and decrypting the data.
It also provides mechanisms for authenticating the parties involved in the communication.
The security of the TLS handshake is crucial for the overall security of the TLS protocol.
Transport Layer Security (TLS) handshake Purpose:
- Initiates a secure communication session between two entities (usually a client and a server) over a network.
- Establishes the parameters for encryption and authentication, ensuring confidentiality, integrity, and authenticity of data exchanged.
Key Steps:
-
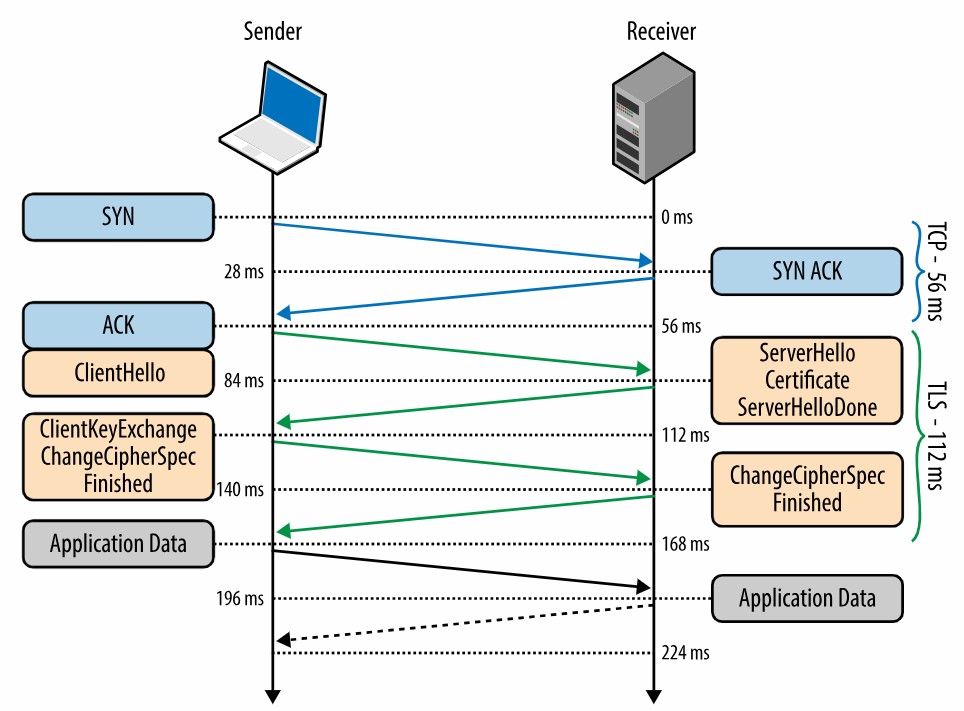
Client Hello:
- Client sends a "ClientHello" message, specifying:
- Supported TLS versions
- Preferred cipher suites (algorithms for encryption and authentication)
- Random data for session key generation
- Client sends a "ClientHello" message, specifying:
-
Server Hello:
- Server responds with a "ServerHello" message, selecting:
- TLS version to use
- Cipher suite to utilize
- Its own random data for session key generation
- Server certificate (containing its public key)
- Server responds with a "ServerHello" message, selecting:
-
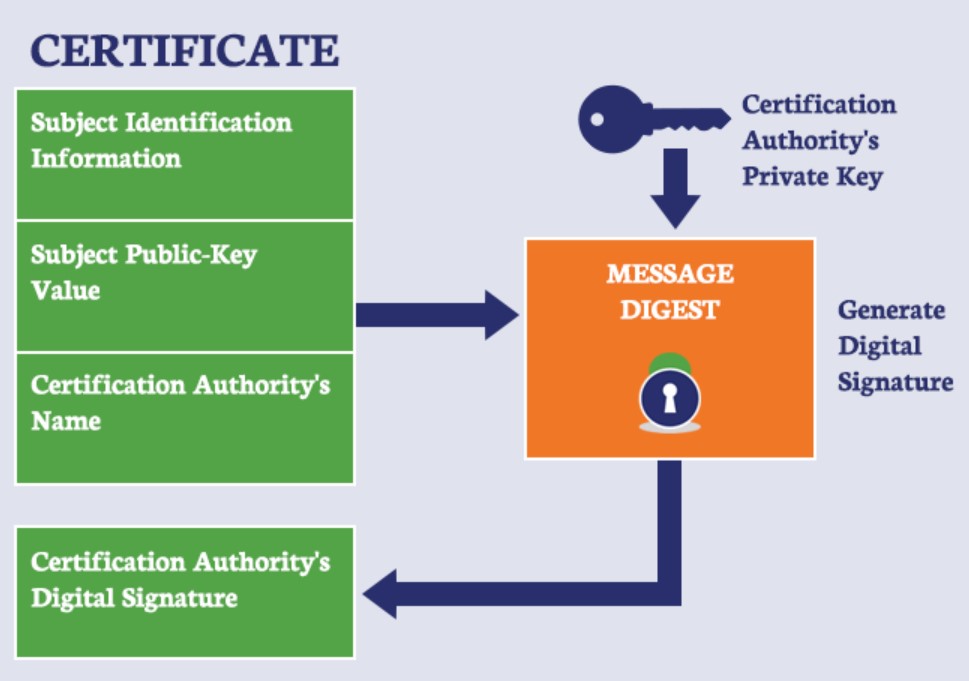
Server Authentication:
- Client verifies the server's certificate using a trusted Certificate Authority (CA).
- This ensures the server's identity and prevents man-in-the-middle attacks.
-
Key Exchange:
- Client and server use public key cryptography to establish shared secret keys.
- These keys are used to encrypt and decrypt subsequent communication.
-
Client Authentication (optional):
- Server may request client authentication using a client certificate.
-
Finished:
- Client and server exchange "Finished" messages, containing a hash of all previous handshake messages.
- This verifies that both parties have the same understanding of the negotiated parameters and prevents tampering.
Additional Details:
- Cipher Suites: Combinations of algorithms for encryption, authentication, and key exchange.
- Session Resumption: Cached session keys can be used to resume a secure session more quickly.
- TLS Versions: TLS 1.3 is the most recent and secure version. Older versions (1.2, 1.1, 1.0) have vulnerabilities and are being phased out.
Benefits of TLS Handshake:
- Protects sensitive data from eavesdropping and tampering.
- Prevents impersonation of servers and clients.
- Ensures data integrity and authenticity.
- Forms the foundation for secure web browsing (HTTPS) and other secure communication protocols.
Enroll Now
- Cybersecurity
- SSL/TLS/HTTPS