Webserver Security
Web server security is crucial to protect your web applications and data from various threats, including cyberattacks, data breaches, and unauthorized access.
Some key aspects and best practices for enhancing web server security:
-
Regular Software Updates: Keep your web server software, operating system, and all installed software up to date. Security patches are often released to address vulnerabilities. Automated updates can help in this regard.
-
Firewall Configuration: Implement a firewall to control incoming and outgoing network traffic. Configure the firewall to allow only necessary traffic to reach your web server.
-
Secure Protocols: Use secure protocols like HTTPS (TLS/SSL) to encrypt data in transit. Secure your server's SSL/TLS configuration and regularly update certificates.
-
Web Application Firewalls (WAFs): Deploy a WAF to filter and monitor incoming web traffic for malicious requests and to protect against various web application attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
-
Access Control: Employ strong access control mechanisms. Limit access to the server through secure authentication and authorization. Use strong, unique passwords and two-factor authentication (2FA) where possible.
-
File and Directory Permissions: Restrict file and directory permissions on the server to ensure that only authorized users or processes can access, modify, or execute them. Regularly review and audit file permissions.
-
Security Headers: Implement security HTTP headers, such as Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and X-Content-Type-Options, to mitigate various web vulnerabilities.
-
Intrusion Detection and Prevention Systems (IDS/IPS): Utilize IDS and IPS tools to detect and prevent intrusions. These systems can monitor server activity for unusual behavior and block suspicious traffic.
-
Security Patches and Vulnerability Scanning: Regularly scan your web server for known vulnerabilities and apply patches promptly. Vulnerability scanning tools can help identify potential weaknesses.
-
Security Plugins and Modules: Depending on your web server software, consider using security plugins or modules specifically designed for enhancing security. For example, ModSecurity for Apache.
-
Log Management: Enable and regularly review logs, including access logs, error logs, and security logs. Log analysis can help detect and respond to security incidents.
-
DDoS Mitigation: Deploy DDoS (Distributed Denial of Service) mitigation solutions to protect your server from overwhelming traffic. This may involve using a content delivery network (CDN) or a dedicated DDoS protection service.
-
Backup and Recovery: Implement regular backup and disaster recovery plans to ensure that you can quickly restore your server in case of a compromise or data loss. Store backups securely, and test recovery procedures.
-
Security Headers: Use security headers, such as Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and X-Content-Type-Options, to enhance protection against common web security vulnerabilities.
-
Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and weaknesses in your web server setup. Address the issues discovered during these assessments.
-
Security Training: Ensure that your staff responsible for managing the web server are trained in security best practices. Human error can be a significant security risk.
-
Restrictive Upload Policies: If your web application allows file uploads, ensure strict policies are in place to prevent malicious file uploads and execution. Restrict file types and scan uploads for malware.
-
Web Server Isolation: If feasible, isolate your web server from other critical infrastructure components. Use separate servers for different services and applications to limit the impact of a security breach.
-
Incident Response Plan: Develop and regularly update an incident response plan to respond to security incidents effectively. Ensure that all staff are aware of the plan and their roles during an incident.
Web server security is an ongoing process. It's essential to stay informed about emerging threats and best practices and regularly monitor and update your security measures to protect your server and the data it hosts.
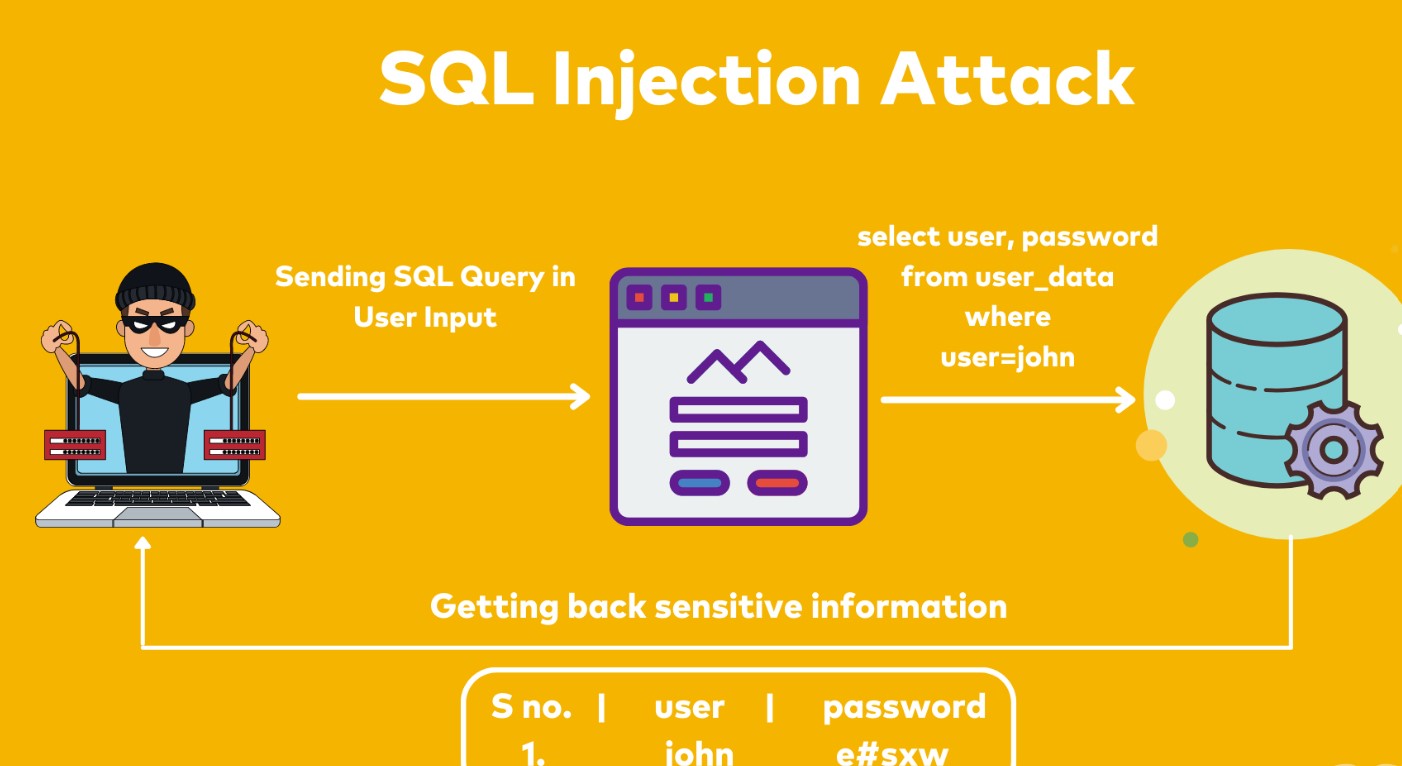
OWASP Top 10 Application Security Risks
| Risk | Description |
| Injection | Injection flaws, such as SQL, OS, and LDAP injection, occur when untrusted data are sent to an interpreter as part of a command or query. The hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization. |
| Broken authentication | Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens or to exploit other implementation flaws to assume other users’ identities. |
| Sensitive data exposure | Many web applications and APIs do not properly protect sensitive data. Attackers may steal or modify such weakly protected data. Sensitive data deserves extra protection, such as encryption at rest or in transit, as well as special precautions when exchanged with the browser. |
| XML external entity | This type of attack parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server-side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts. |
| Broken access control | Restrictions on what authenticated users are allowed to do are not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data, such as access other users’ accounts, view sensitive files, modify other users’ data, and change access rights. |
| Security misconfiguration | Security misconfiguration is the most common issue in the data, which is due in part to manual or ad hoc configuration, insecure default configurations, open S3 buckets, misconfigured HTTP headers, error messages containing sensitive information, and not patching or upgrading systems, frameworks, dependencies, and components in a timely fashion. |
| Cross-site scripting (XSS) | XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or when it updates an existing web page with user-supplied data using a browser API that can create JavaScript. XSS allows attackers to execute scripts in the victim’s browser, which can hijack user sessions, deface websites, or redirect the user to malicious sites. |
| Insecure deserialization | Insecure deserialization flaws occur when an application receives hostile serialized objects, which can lead to remote code execution. Even if deserialization flaws do not result in remote code execution, serialized objects can be replayed, tampered, or deleted to spoof users, conduct injection attacks, and elevate privileges. |
| Using components with known vulnerabilities | Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts. |
| Insufficient logging and monitoring | Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Breach studies show that the time to detect a breach is over 200 days, and detection is typically based on the work by external parties rather than internal processes or monitoring. |
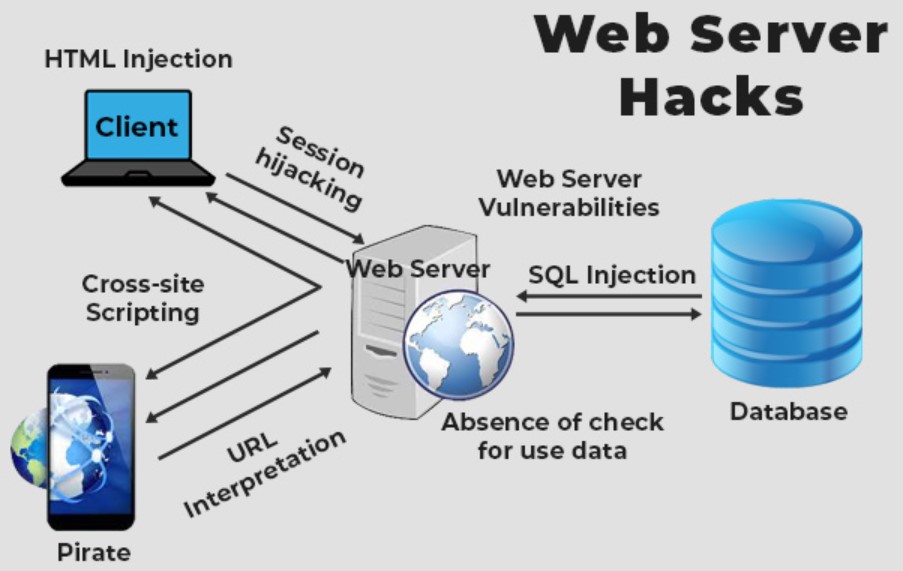
Web server security is the practice of protecting web servers from unauthorized access, use, disclosure, disruption, modification, or destruction. Web servers are a critical component of the internet, and they are often targeted by attackers.
There are a number of ways to secure web servers:
- Keep software up to date. Software vendors regularly release security patches to address vulnerabilities. It is important to install these patches as soon as they are available.
- Use strong passwords and authentication methods. Passwords should be at least 12 characters long and include a mix of upper and lowercase letters, numbers, and symbols. Two-factor authentication (2FA) can also be used to add an extra layer of security.
- Disable unused services and ports. Attackers can exploit unused services and ports to gain access to web servers. It is important to disable any services or ports that are not being used.
- Configure firewall rules. Firewalls can be used to restrict access to web servers. It is important to configure firewall rules to only allow authorized access to the server.
- Use a web application firewall (WAF). A WAF can be used to protect web servers from attacks such as SQL injection and cross-site scripting (XSS).
- Monitor web server logs. Web server logs can be used to detect suspicious activity. It is important to monitor logs for signs of attack.
- Have a backup plan. In the event of a security breach, it is important to have a backup plan in place. This will allow you to restore your data and get your website back online quickly.
By following these best practices, you can help to secure your web servers and protect your data from attackers.
In addition to the above, here are some specific web server security hardening tips:
- Remove unnecessary software. The less software that is installed on a web server, the less attack surface there is for attackers to exploit.
- Disable directory listing. Directory listing can allow attackers to see what files are stored on a web server.
- Restrict access to sensitive files. Sensitive files, such as configuration files and databases, should only be accessible to authorized users.
- Use a content management system (CMS) that is known to be secure. CMSs are often targeted by attackers, so it is important to use a CMS that is known to be secure and to keep it up to date.
- Educate users about security best practices. Users should be aware of the risks of phishing attacks and other social engineering attacks. They should also be aware of the importance of using strong passwords and not sharing their passwords with others.
By taking these steps, you can help to make your web servers more secure and protect your data from attackers.

Enroll Now
- Python Programming
- Machine Learning